Salt Typhoon strikes South Africa: critical industries targeted in global cyber espionage campaign
A Chinese hacking group, Salt Typhoon (Earth Estries), has targeted South Africa in a global cyber espionage campaign affecting telecom, government, and tech sectors across 12 nations. Using advanced malware and stealth tactics, the group remains undetected for years, posing severe security risks.

Earth Estries, also known by aliases such as "SALT TYPHOON" and identifiers linked to their operations, is a Chinese-based Advanced Persistent Threat (APT) group specializing in long-term cyber espionage. Operating since at least 2023, the group has targeted critical industries worldwide, including telecommunications, government agencies, and technology providers. Their sophisticated techniques and use of shared malware, including tools like "SNAPPYBEE" and "DEMODEX," have made them a formidable and elusive cyber adversary.
A report published by Trend Micro, "Game of Emperor", reviews the Cyber Attack known as Earth Estries, a sophisticated hacking group conducting long-term cyber espionage on critical industries worldwide.
This Advanced Persistent Threat (APT) group, believed to be based in China, has targeted telecommunications, government agencies, technology providers, and non-profits, impacting regions including Asia, the Middle East, the United States, and South Africa since at least 2023.
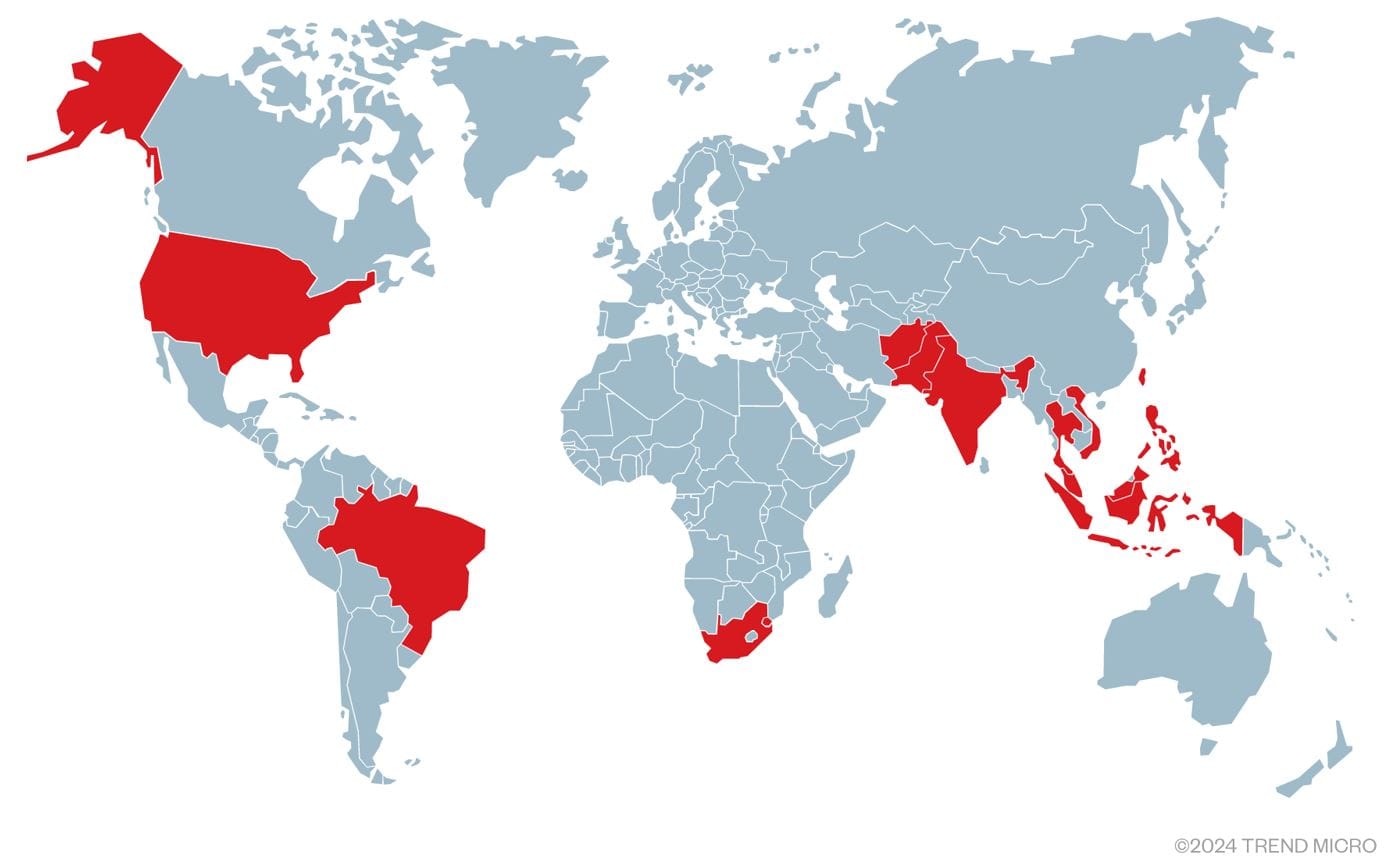
Earth Estries, has compromised over 20 organizations spanning telecommunications, technology, consulting, chemical, transportation, government, and non-profit sectors. Victims of this sophisticated Advanced Persistent Threat (APT) group have been identified in countries which include Afghanistan, Brazil, Eswatini, India, Indonesia, Malaysia, Pakistan, the Philippines, South Africa, Taiwan, Thailand, the United States, and Vietnam. The scale and scope of the group's activities underscore the pervasive threat they pose to critical industries worldwide.
Earth Estries exemplifies APT groups, which are well-funded and methodical hacking teams focused on gathering intelligence over months or even years. Unlike opportunistic cybercriminals, APTs employ stealthy, ongoing intrusions to access and exfiltrate sensitive information.
Earth Estries' Unique Tactics employed are:
- Prolonged Intrusions: The group embeds itself within networks for extended periods, often remaining undetected for years to observe, collect, and steal sensitive data.
- Targeted High-Value Sectors: By infiltrating telecommunications networks, Earth Estries can potentially intercept communications, monitor individuals, and map organizational structures. Their focus on government and technology sectors underlines the strategic value of their targets.
- Shared Tools and Techniques: Using advanced malware such as “SNAPPYBEE,” “DEMODEX,” and “MASOL RAT,” Earth Estries capitalizes on a "malware-as-a-service" ecosystem, sharing tools with other Chinese APT groups. This collaborative approach complicates efforts to attribute attacks to specific perpetrators.
- Adaptability: The group leverages known software vulnerabilities, referred to as “N-day vulnerabilities,” exploiting weaknesses before patches are applied. They also use built-in system tools, a tactic known as “living-off-the-land,” to minimize detection.
Earth Estries often gains initial access through publicly accessible servers by exploiting vulnerabilities in widely used systems, including VPN servers, Microsoft Exchange email platforms, and firewalls. Once inside, they expand their foothold by deploying:
- Backdoors: Secret network entry points allowing repeated access.
- Rootkits: Deeply embedded software that evades detection and enables long-term data theft.
Earth Estries seeks a variety of sensitive information, including:
- Government and military intelligence.
- Business and intellectual property data.
- Telecom records that can reveal communication patterns and organizational hierarchies.
Their operations suggest a corporate-like structure, with specialized teams handling malware development, infrastructure management, and infiltration. This model reflects significant resources and advanced capabilities.
Despite global warnings about the risks posed by Earth Estries, South Africa has yet to issue public advisories or guidance to counter these threats. Unlike other regions that recommend using encrypted messaging or bolster telecom security, South African authorities remain conspicuously silent.
Additionally, there are indications that telecom operators in South Africa may not be reporting breaches to regulators, as required by law. A lack of transparency raises concerns about whether customers, law enforcement and regulators have been notified of potential security compromises as required by RICA, POPIA and the Cyber Crimes Act. Foreign operators attacked by Earth Estries continue to struggle to eliminate the group’s presence from their infrastructure, including the United States.
Are South African telecommunications operators fully aware of the threat? Have they adequately communicated risks to their customers? And most urgently, are end users unknowingly impacted by this global espionage campaign?