Salt Typhoon: The Unraveling of a Global Cybersecurity Catastrophe
Salt Typhoon, a Chinese state-backed hacking group, infiltrated global telecom operators, accessing sensitive data and wiretap systems. This breach, deemed the worst in telecom history, underscores significant vulnerabilities in critical infrastructure.

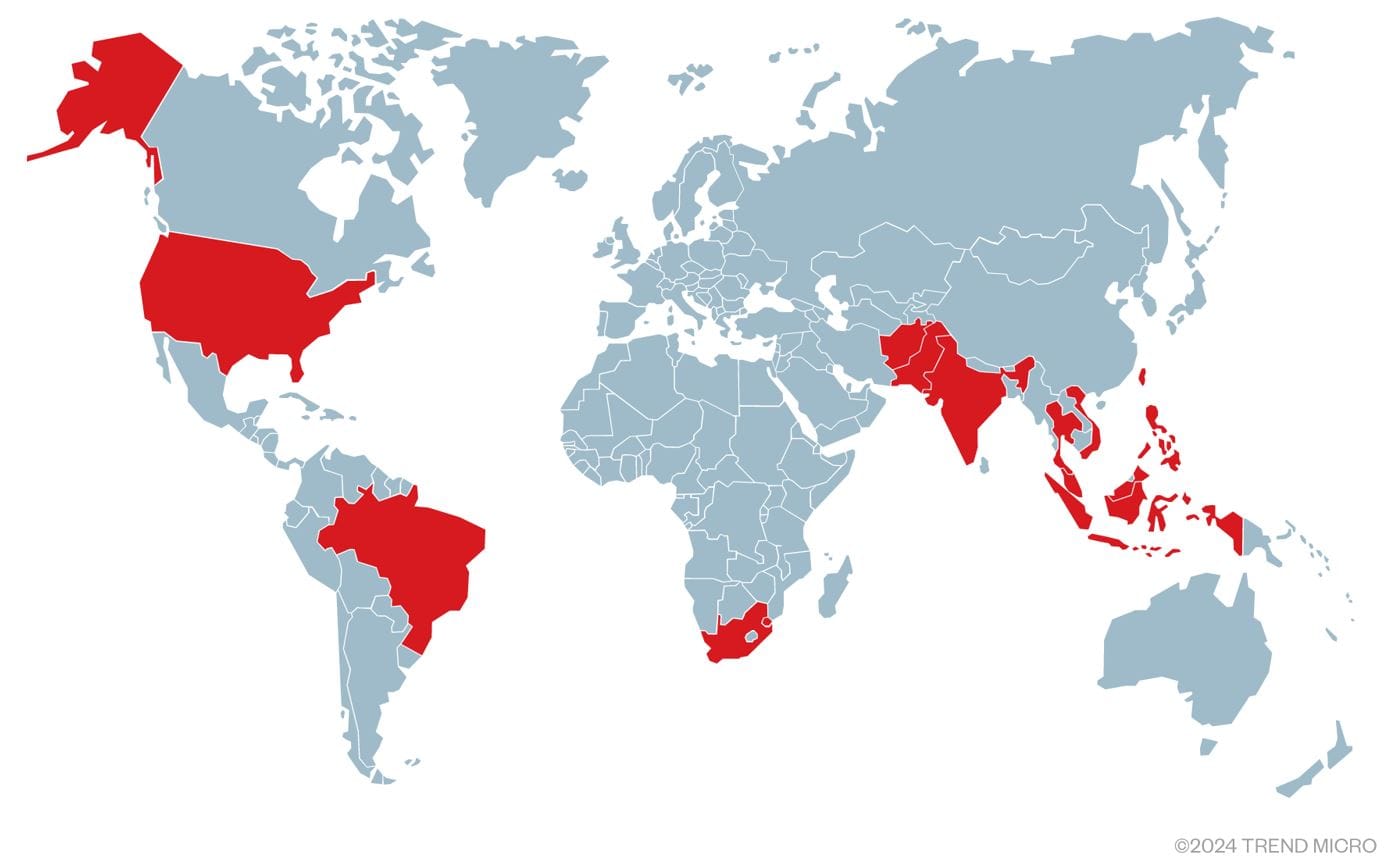
CAPE TOWN - 10 Jan 2025. The Salt Typhoon cyberattack has become one of the most significant breaches of critical infrastructure in recent memory. What began in late 2024 as a series of targeted intrusions at nine major U.S. telecommunications companies quickly spread across continents, exposing systemic vulnerabilities in digital communications networks. Now linked to more than 80 compromised telecom providers worldwide, the hack underscores how potent and pervasive modern cyber espionage campaigns can be especially when orchestrated by a well-resourced, state-backed entity.
Also Read: Salt Typhoon strikes South Africa: critical industries targeted in global cyber espionage campaign
The Salt Typhoon hack initially centered on prominent providers such as AT&T, Verizon and Lumen Technologies. Within months, investigators discovered it had also compromised systems in at least 20 additional countries. Security researchers describe this expansion as both rapid and methodical, capitalizing on unpatched vulnerabilities that, while known to the cybersecurity community, had not been adequately addressed by telecom operators. These oversights allowed Salt Typhoon to establish and maintain persistent access to sensitive networks.
Among the first of the twelve (12) nations initially affected, was South Africa, where the breach appears to have gone unreported.
Despite clear requirements under the Protection of Personal Information Act to notify affected customers of data exposure, there has been no public disclosure from telecom companies or the government. This silence has left millions of South Africans uncertain about the status of their personal data, raising concerns about both individual privacy and broader national security implications.
Global efforts to contain Salt Typhoon have varied widely. In the United States, some telecommunications firms, including T-Mobile, report successful containment of the rootkit code. Others continue to grapple with eradicating the threat entirely. The White House has publicly urged executives to coordinate a swift response, calling for tighter security protocols to prevent future incidents. Still, the hack exposes a troubling reality: cybersecurity standards and practices differ considerably across the industry, leaving gaps that sophisticated adversaries can exploit.
The FCC went further and publicly advised mobile users to use encrypted messaging and voice calls via IOT services such as WhatsApp and Telegram.
Salt Typhoon’s reach now spans Europe, Asia and the Indo-Pacific, prompting coordinated responses from agencies in Australia, New Zealand, Canada and the U.S. Collectively, they have issued guidance on hardening telecom networks against the tactics Salt Typhoon employs. Officials emphasize patching vulnerabilities in widely used networking hardware.
The group’s ability to intercept voice and messaging traffic along with extracting large volumes of proprietary or sensitive data has escalated concerns about espionage and national security on a global scale.
Investigators say Salt Typhoon relies on a Windows kernel-mode rootkit called Demodex that enables deep-level system access. By embedding itself in the operating system, Demodex allows attackers to remain undetected for extended periods, monitor internal communications and exfiltrate data. The operation has also used anti-forensic methods to erase digital footprints, adjust tactics dynamically and blend in with legitimate network traffic. While many of the exploited vulnerabilities had known fixes, the incident reveals critical lapses in how organizations apply security updates in high-stakes environments.
Salt Typhoon’s links to a Chinese state-backed team differentiate it from typical cybercriminal operations. Access to advanced technology, skilled personnel and extensive funding indicates a long-term strategic objective rather than a short-term, profit-driven motive. With the capacity to run prolonged campaigns undeterred by financial constraints, the group has combined stealth and persistence with unrelenting sophistication.
The hack has intensified debate about national cybersecurity in the United States, where some lawmakers urge restricting Chinese technology in critical infrastructure. Meanwhile, billions of dollars in potential damages are at stake for telecom companies now facing remediation costs, possible legal action and reputational fallout.
The breach’s persistence also spotlights industrywide vulnerabilities that may lead to tougher regulations and mandatory reporting on network intrusions.
The fallout from Salt Typhoon serves as a stark reminder of how interdependent and fragile global digital ecosystems have become. The incident demonstrates a pressing need for coordinated international efforts, stronger regulatory frameworks and a cultural shift within organizations, in which cybersecurity is prioritized at every level. While several telecom providers have started to implement more stringent controls and frequent patch cycles, many experts warn this is merely a first step. Given the steady drumbeat of sophisticated attacks worldwide, proactive strategies are vital to stave off another large-scale intrusion.
Nature of the Operation: Core Tactics
Stealth by Design - Salt Typhoon’s methods center on remaining undetected. Through rootkits like Demodex, attackers maintain a minimal footprint, making it difficult for standard antivirus or intrusion detection systems to identify their presence.
Corporate Data Theft - Analysts believe the primary target is proprietary corporate and governmental information, including strategic plans, intellectual property and sensitive communications. Stolen data can be used for economic advantage or to inform policy and geopolitical strategies.
Intercepting Voice and Messaging - Salt Typhoon reportedly accesses telecommunication networks in ways that let it intercept voice calls, SMS messages and potentially even encrypted channels. This real-time intelligence poses critical security implications for governments and private businesses alike.
As an entity supported by a nation-state, Salt Typhoon benefits from extensive funding and expertise. Such backing enables the group to pursue long-term objectives, adapt techniques on the fly and coordinate multiple, simultaneous breaches across diverse targets.
Salt Typhoon represents a chilling benchmark in state-sponsored cyberattacks, both in scale and sophistication. With its ability to burrow deeply into telecom networks and harvest sensitive data for extended periods, this operation has shattered assumptions about the security of vital communications infrastructure. The global response ranging from legislative debate to technical countermeasures reflects growing awareness that cybersecurity demands a unified, agile approach. As Salt Typhoon’s full impact continues to unfold, it serves as a crucial warning that the next evolution in cyber warfare may already be at hand.